Bulk Assign Categories to Multiple Posts
October 14th, 2008
Here’s a cool new wordpress plugin that allows you to assign one or more categories to multiple posts in a single shot, with or without preserving existing categories.
This plugin will be very useful when you are migrating to your own wordpress blog, hosted on your domain. The default wordpress functionality is that, you can assign new categories to posts only by editing each post and changing the category assigned to it. So, if you have a large number of posts, then it will be a nightmare.
Enter this plugin.
With this plugin, assigning multiple categories to one or more posts is a breeze. Pop the plugin’s PHP file to your wordpress plugin directory, activate it and click on “Assign Categories” under the Manage menu. The page will show the list of available categories, followed by the available blog posts. You can select the categories, select the required posts and then click on “Assign Categories” at the bottom of the page. Now, all your posts will be assigned the new categories.
The plugin is licensed under GPL v2 (the same as wordpress).
Download the plugin, take it for a test drive and let me know.
Microsoft TechVista
October 2nd, 2008
Microsoft Research (MSR) India conducted TechVista yesterday, a symposium by MSR to showcase some of the hottest research that’s been happening. The talks were interesting and so were the posters presented by various students from top notch colleges, some of whose research is sponsored by Microsoft.
After the usual keynote, the real talk began by 10.45 AM. The talk was about the “Future of Computing” by Dr. John Hopcroft. It was a very insightful talk with details about ‘the cloud’ that I could relate to; and also about information storing and retrieval in digital form. The next talk was by Dr. Richard Szeliski about “Weaving the World’s Photos”. This talk was more about Photosynth and the technology and algorithms that go behind it. The talk was simply awesome; especially the place when they mentioned about the SIFT and RANSAC algorithms. SIFT determines similar points in 2 photos taken from different angles while RANSAC is able to stitch those points together and form a 3D model of the image. Considering the fact there are 1000s of photos online for a popular place (E.g. Taj Mahal), with photos taken from different angles, the SIFT and RANSAC algorithms brings about the 3D model of the place. Then these points are optimized and the resulting images are stitched together. When pictures are more detailed and where users have tagged those details, these pictures are used when users zoom in and zoom out of the 3D model. It also removes all the “noise” from the photographs and gives an almost seamless 3D experience.
The next talk I attended was by Dr. Shafi Goldwasser about program obfuscation and one-time programs. I could related to this talk because of my very recent experiment 😀 and paid full attention to this talk. I was smiling when one of her slides contained the last paragraph of this blog post from YUI blog. Many points in her slide were eye-opening such as ROKs and the slides that said where obfuscation fails.
It was lunch now. Somehow, most of these conferences mangle up lunch so badly that we want to give out a blood curdling yell. As soon as the morning session talks were over, myself and a few guys walked over to the Professors and were asking them a few doubts. By the time we went for lunch, most of the good dishes were over. So were the desserts 🙁
The talk immediately after lunch was some marketing blah blah about MSR that was putting me to sound sleep. I woke up and went to the poster presentations to check out what the Ph.D students had done. Some of the posters were really cool! I liked the ones on “Understanding the dynamics behind evolution of stable peer-to-peer networks” by Bivas Mitra from IIT-KGP, “Secure Distributed Computation and Communication” by Arpita and Ashish from IITM and PULRP by Deepthi and Kannan from IITB. It was about an hour by the time I finished looking through the posters. With my sleep vanished, I headed to main hall again to check out the next talk.
This talk was about “Computational Camers” by Dr. Shree K Nayar. It was just awesome! When I was college, I did a paper on Digital Image Processing and almost cried because of the complex equations 🙂 All of those were coming back in my head when this talk was going on. May be if I had known earlier, I would have applied for MSR as soon as I had passed out.
With this talk getting over, one of my friends who was a finalist of my batch’s MSAPP had come to the venue. Just as myself, Dhaval and Subhamoy were getting intro’d to him, we delved deep into quantum and relative physics, with a bit of astronomy thrown in. That twisted my brain in some crazy ways. Our discussion happened for more than 2 hours and I learnt a lot more from this discussion than from the ones that were happening inside at this time.
Oh! while I was talking to Subhamoy, he casually mentioned this story. His mobile had fallen in water & when he switched it on, it got short circuited. So, he removed the panels, took the mobile circuit to this lab, found the short circuits and resoldered everything again in their proper places. He is still using that same phone. THAT WAS AWESOME!
All-in-all, it was a day spent very well 😀 I enjoyed every moment to the core.
Dissecting iMobile – Security Analysis of ICICI Mobile Banking App
September 27th, 2008
ICICI Bank’s iMobile website has some of the worst server side validations ever, which is what prompted me to download the mobile app’s JAR file, study it in detail and write this post. According to the website, until the Reserve Bank of India comes out with mobile banking guidelines and approves it, mobile banking is supposed to be halted. Technically, it means that, all existing users shouldn’t be able to use the service what-so-ever and new user signups should be prevented & a notification stating that they should retry later should be shown.
Therefore, in this scenario, I shouldn’t have been able to download the app to my mobile device. The website of ICICI fails in not enforcing this by providing the following ways:
- Existing users who have already installed the app are given an option to ‘Upgrade’ from within the mobile app itself. This opens up a webpage in the phone’s native browser, whose URL is http://mobile.icicibank.com/upgrade?version=null.
- The actual iMobile website has some stupid javascript validation, which is very easy to bypass using modern browsers. Heck, just by browsing the HTML source code of the page, you will be able to easily find the URL for the application JAR files. Put 2 and 2 together and you will be able to download the app.
Which brings me to explain Step 2 in detail:
document.jump1.action="https://infinity.icicibank.co.in/web/apps/"+fileName;. That line pretty much gives away everything. All you have to do is, navigate to the above mentioned URL and append a filename to it for download.What filename do you have to give and How?
Where ICICI Bank failed?
- They should have disabled the link mentioned in #1 above and replaced it with some text that says, “RBI mobile banking guidelines blah blah…”. But some clever users will bookmark the link to the JAR file and try to access the JAR file by bypassing the link itself. When they do that, the web server should return a “404 – Resource Not Found” error. Got it? Implementing this is pretty simple.
- There shouldn’t have been such a lot of useless javascript on the page. Firstly, they should have removed the device selection drop down box. Secondly, they should have replaced this page with an alternative. Thirdly, this mobile banking link should have been removed in the home page itself. Fourthly, they should have validated on the server for JAR file downloads and should have displayed the “404 – Resource Not Found” error page.
- Ok. Leave aside #1 and #2. At least the mobile app should have thrown soft errors when users try to access mobile banking from the JavaME app. Any bank would store all activity data for a certain period of time. So when you access the bank’s service from a mobile device, the server software surely knows about it, which means, the server software should have returned errors to the user instead of allowing the user to do transactions.
- There’s one more bug in the app itself. When you launch the app, it will prompt you to sync the data on the device to its servers for faster access the next time. When you click “OK” to synchronize, it will wait for a few minutes and show a message as, “There is no data to synchronize”. When you proceed further and try to access your info, it will again prompt you to sync the data. That’s frustrating. Either you should sync the data properly or you should access the server every time over a secure channel. As simple as that. That’s not followed too.
That was a long post already 🙂 We still have some more to go. Lets take a break.
Back? Ok 😀 Now, lets dissect the actual JAR file and look into the technical details of its implementation.
The Manifest File:
Another important item is, “MIDlet-Name” property in the manifest. This property determines what name the user sees after he installs the app on his mobile. Using the same name, when future upgrades are made available, the app is just replaced in place of the old one, which means, if you modify the “MIDlet-Name” property and install the app again, you will have 2 copies of the same app. THIS SHOULD NEVER BE ALLOWED FOR A HIGHLY CRITICAL FINANCIAL APPLICATION. Isn’t it? As an example, try changing the MIDlet-Name of the Yahoo! Go JAR file and try to install the app again on your mobile. My E51 shows an “Invalid JAR” error message because of MD5 sum checks etc.
Some more Holes:
What should the bank do here?
- Shouldn’t allow the installation of 2 apps of the same JAR with different names. Take this example of the Yahoo! Go JAR file.
- I guess these mobile providers’ socket URLs are used for a one time basis to send verification SMS. If that be the case, they shouldn’t be present in the manifest file for a variety of reasons that I won’t discuss here.
- There’s an interesting property named “WSCDomainName” in the manifest file. I guess it expands to “Web Service Client Domain Name”, though I’m not sure about it. Suggestion: Encrypt the name value pairs.
- Most importantly, sign the application using the Java Signed program. C’mon, users are doing financial transactions and a signed app will increase their confidence of using this application.
Suggestion for Users:
Thats about it !
Of course, this blog post can’t be termed as a full fledged security analysis. But most of what has been ignored by the bank are mere basics. They must have more secure systems in place.
If you liked this article, kindly do me a favour by digging it. Thanks for your time.
RSS Feed Proxy – Finally one data format to parse all feeds
July 12th, 2008
Hey guys! I discovered two feed proxies.
- http://www.netvibes.com/proxy/feedProxy.php?test=1&url=__FEED_URL__
- http://my.live.com/cfw/news.aspx?fetchurl=__FEED_URL__
Replace the __FEED_URL__ with the feed URL of your choice. Of the two feed proxies above, I like Netvibe’s proxy as the best because of the following reasons:
- Feed output is JSON. This means that, netvibes has done all the necessary work to convert feeds of any type (RSS, ATOM, RDF etc.) into JSON.
- If you are writing a script to examine feeds from various sites, you have only one data structure to deal with 😉
- Almost all programming languages support JSON. Refer to www.json.org for JSON libraries available for various programming languages.
- JSON by itself is very lightweight and eliminates most of the overhead of XML, thereby preserving bandwidth.
- A simple program in VB.NET to parse a JSON structure and get the required feed data in a Dictionary datatype is only about 9 lines of code. In Ruby, it will be even lesser. Compare the same with XML output. Even though feed parsers are available, you have to create your own wrapper above everything to get everything to work out properly. Reuse what you already have (DRY Principle). Netvibes has already done the bull work to convert all kinds of feeds into a common format.
- Best of all, no authentication is necessary to access these links 😀
Live.com’s feed proxy returns the actual feed output. So, if the feed you are referring to gives RSS output, this proxy returns that. The same happens with ATOM, RDF etc. Keep watching this space. I will update the post with other feed proxy URLs that I encounter. If you go across any, please mention them in the comments section.
Â
An ode to Ruby
June 21st, 2008
One of my juniors in college named Satish has written this small wonderful piece on Ruby (programming language).
Ruby makes a programmer smile
even when he’s using while
all the if’ and else’ and do’
reduces the work you do
kernel methods work like charm
conventions make work a form
all the while you reap the fruits
everyone gives java the boots!
Cool ! Ain’t it? 🙂
How To: Open a root terminal in Ubuntu
June 10th, 2008
I was playing around with Ubuntu & installing a few stuff from the terminal. One problem that quickly became a pain in the rear is that, I had to `sudo` everytime and give a password whenever a command that required admin privileges had to be run. Since, I was installing a few stuff, almost all commands required admin rights. So, without much ado, here’s how to open a terminal with permanent root privileges.
- Press Alt+F2. The “Run Application” dialog will pop up.
- Type “gnome-terminal” in the dialog and press “Enter”. This will open a new terminal window without admin rights.
- Now, in the new terminal window, type “sudo gnome-terminal”. You will be asked for your password. Give your password and press “Enter”. A separate terminal window with root privileges will open now. This is immediately visible because the usual “$” prompt changes to a “#” prompt.
There you go, 🙂 three cool steps to have your terminal with admin rights. If you press “Ctrl+Shift+N” from this new terminal, it will open another terminal window, which also has root privileges.
Â
NTFS, Gmail Keyboard Shortcuts
April 18th, 2008
Two things today:
Few days ago, I was searching for information on NTFS and found 2 amazing articles from the good old MSJ (Microsoft Systems Journal). The links are below. Do go through them when you find time. Even though the articles are old, they offer a wealth of information.
- Windows NT 5.0 File System – http://www.microsoft.com/msj/1198/ntfs/ntfs.aspx
- NTFS Change Journal – http://www.microsoft.com/msj/0999/journal/journal.aspx
There are lot more articles available. I will post the links as and when I read them. Nice stuff !
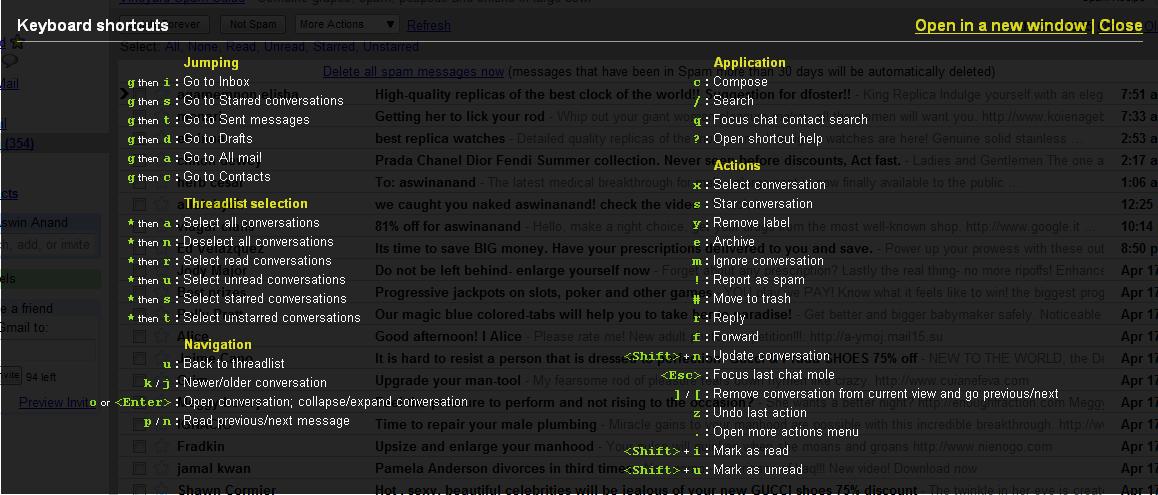
As you already know, I have enabled keyboard shortcuts on my gmail account. Gmail actually shows you the list of available shortcuts right inside your mailbox, without us having to visit the keyboard shortcuts page. To access the list of keyboard shortcuts, you need to press “?” key, which is “Shift + /“. You will get the translucent black popup as shown in the below screenshot. You can press any key to close it.
Click the image to see a larger version.
Blog Subdomains
January 21st, 2008
Hey friends, lots of people have been asking me why I have two separate blogs (tech and non-tech), while I could have them both in the same place. I would like to answer that in 2 ways:
- Both the blogs are in the same place. All the posts in the proper order can be viewed at http://www.aswinanand.com/blog.
- Subdomains such as http://blog.aswinanand.com/ and http://tech.aswinanand.com/ exist for backward compatibility.
Long back, when I started blogging, while many readers enjoyed reading my blog, some of them didn’t like the tech content in between. Hence, I moved the tech content to another blog. Finally, when blogger for domains came in, my tech and non-tech blogs became available at the links mentioned above. Hence, for those users who had subscribed to this blog, I didn’t want them to lose out.
So, the actual blog url is http://www.aswinanand.com/blog and the tech and non-tech blog show contents from the space, just separated by tags. This, along with the magic of htaccess and 1 php file, many things can be changed so that the permalinks will be available in a better fashion. Moreover, when I want to do a post in both the tech and non-tech blogs (like this one), I can just add the 2 tags to this post and they are available in both the blogs. Change the post once and the change is visible in both the blogs (if you visit them separately). Configuring a mobile client for the same is very easy and all this can be done in a single space 😀
When this blog pings certain links after an update is made (like technorati etc.), the blog url goes as http://www.aswinanand.com/blog and not blog.aswinanand.com or tech.aswinanand.com. Therefore, when someone is redirected by search engine results, they will just visit the full blog and not the other ones 😉 How’s that?
When template is changed, the change is visible all throughout 🙂 and looks very uniform. So…. that’s the reason for both the blogs being “virtually separate” hehe…
Server Side Validation – Importance
January 5th, 2008
Time and again, there are countless number of articles written on not to trust user input and do a server side validation of all input. There are quite a lot of libraries in all imaginable languagues that make server side validation very easy.
But time and again, every other site pops up that have only client side validation. One such site is http://www.cinetickets.in/. The site has a registration page. The first field required is called “user id” and we have to give our phone number. What crap!
On firefox, there is a superb toolbar called the Web Developer toolbar. Once installed, you can play with all components of the page, including cookies, headers, scripts … anything. That “user id” field accepts only numbers. Hence, I disabled all javascripts on the page, entered some text, filled up the rest of the page and clicked on Submit. Guess what? The page registered perfectly. With scripts disabled, I’m able to login also.
I went back to the registration page again (with all javascript disabled ofcourse!) and clicked on Submit without giving any data. The site throws an error message saying that the user is already registered. LMAO.
With such crappy validation schemes, I’m pretty sure that there are no server side validations being done as well. They are just taking data from the client and pushing them into a database (most probably MySql) without sensitive data being encrypted (they accept credit card details etc.). Assuming I’m a hacker, the site can be brought down within a few minutes! Looks like the CineTickets website is programmed by a company called EvinceTech.com. Don’t ever outsource your website development there. It’s very easy to conclude that they are a shit load of programmers.
Anyways, I found an awesome PHP script some days ago that filters out dangerous tags from strings. The script is available here. I encourage everyone to use it, if you can’t/don’t-want-to write one on your own.
Java ME – OTA Problems
December 7th, 2007
OTA means “Over The Air provisioning” – which also means downloading a Java ME app directly on your mobile phone. Therefore, OTA means, just plain downloading. That’s all!
But there are some problems. I developed a simple application using netbeans 6 and wanted to do a OTA deployment of the application. Hence, both the JAD & JAR files were uploaded to the web server. Now, I opened the web browser on my mobile and typed out the url of the JAD file. Usually, there is a property called on the JAD file called MIDlet-Jar-URL. It contains the link to the jar file. E.g. If suppose the JAD is located at http://aswinanand.com/app.jad, the MIDlet-Jar-URL in the JAD file will contain related properties of the JAR file including its download link.Â
Hence, when a mobile identifies a JAD file, it will search for MIDlet-Jar-URL property, fetch the download link & download and install the application on your phone. What happened here was that, even though the JAD file was in perfect condition, it just got rendered as plain text on the mobile’s browser. The JAR was not downloaded and installed. Soon, I found out that the MIME type of JAD was different and that, for JAD files, “Content-Type” HTTP header has to be set to “text/vnd.sun.j2me.app-descriptor“. For JAR files, the “Content-Type” HTTP header has to be set to “application/java-archive“.
My web server runs apache. Hence, I just created a .htaccess file with the following entries:
AddType text/vnd.sun.j2me.app-descriptor .jadAddType application/java-archive .jar
Now the JAD file was recognized perfectly by the phone :-). The JAR was downloaded and installed properly :D. More info on OTA can be obtained from here.